Today we are happy to announce the release of version 0.7.88. This release, in addition to bug fixes and minor adjustments, brings the following improvements to Malcat:
- MSI Installers analysis
- Scripting interface documentation
- Joe Sandbox online threat intelligence lookup
MSI Installers analysis
The biggest change is the new MSI decompiler that we added to Malcat. MSI installers have been abused by malware authors for some time now. While the MSI format is based on the OLE/CFB file format and thus supported by Malcat, we were not able to inspect the content of the relational database inside the installers, which is a requirement for efficient MSI analysis. But since 0.7.88, you can use the new MSI decompiler (hit F4) to dump the content of those tables:
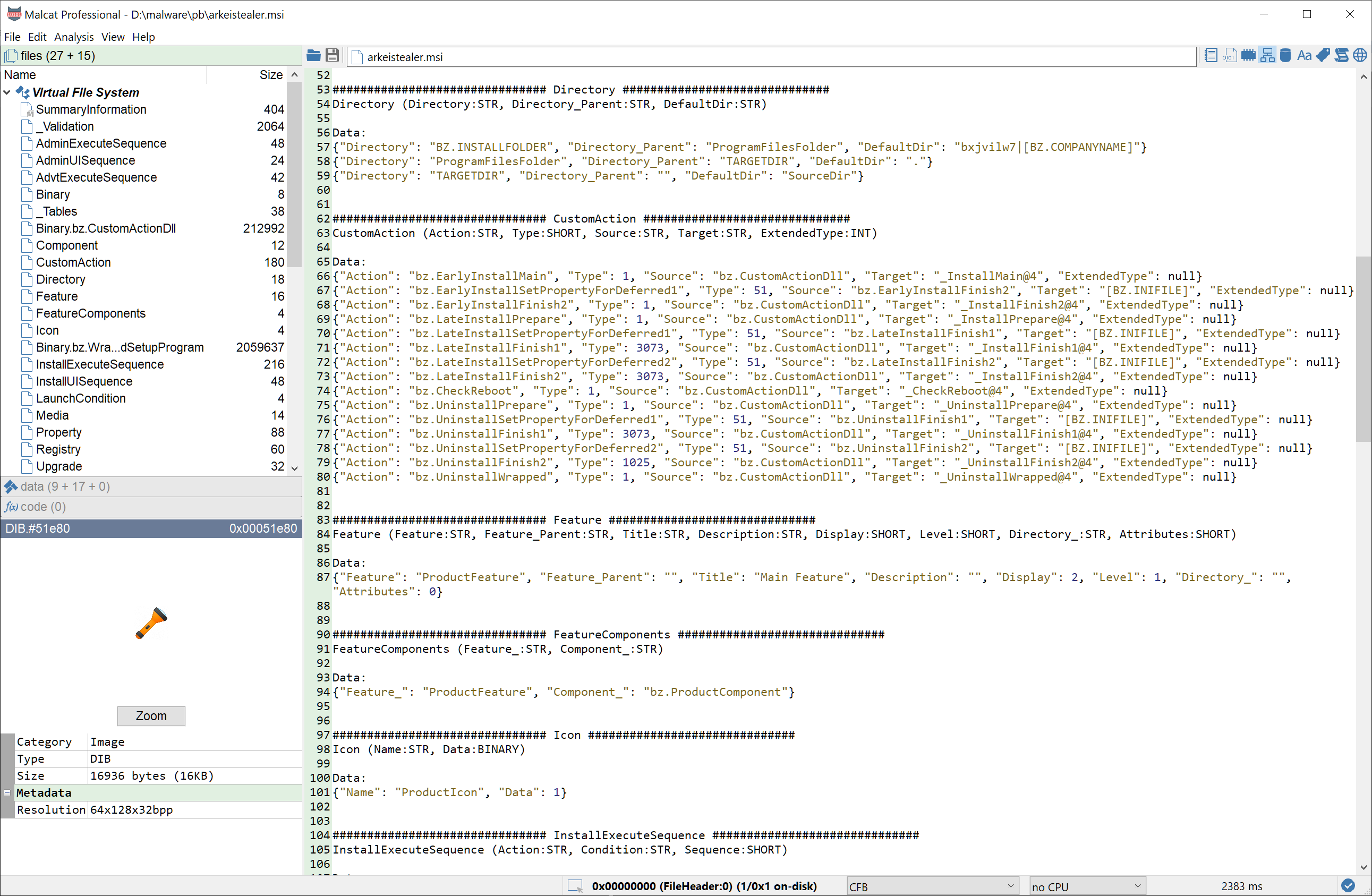
The content of the database is also accessible to the scripting interface via the malcat.analyzer.msi_db python object when analysing MSI files (have a look at the file data/filetypes/CFB_msi.py for more information). This brings us to the next improvement:
Scripting interface
While the documentation is still under construction, progress has been made regarding the python scripting interface. It is now fully documented inside Malcat's inline help (hit Ctrl+H) under the Scripting category. If you are new to scripting, we advise you to first play with the toy script that is displayed when you enter the script editor (F8). More scripting in action can also be seen by inspecting the python files in data/scripts/ and data/anomalies/ (only for paid versions for the later).
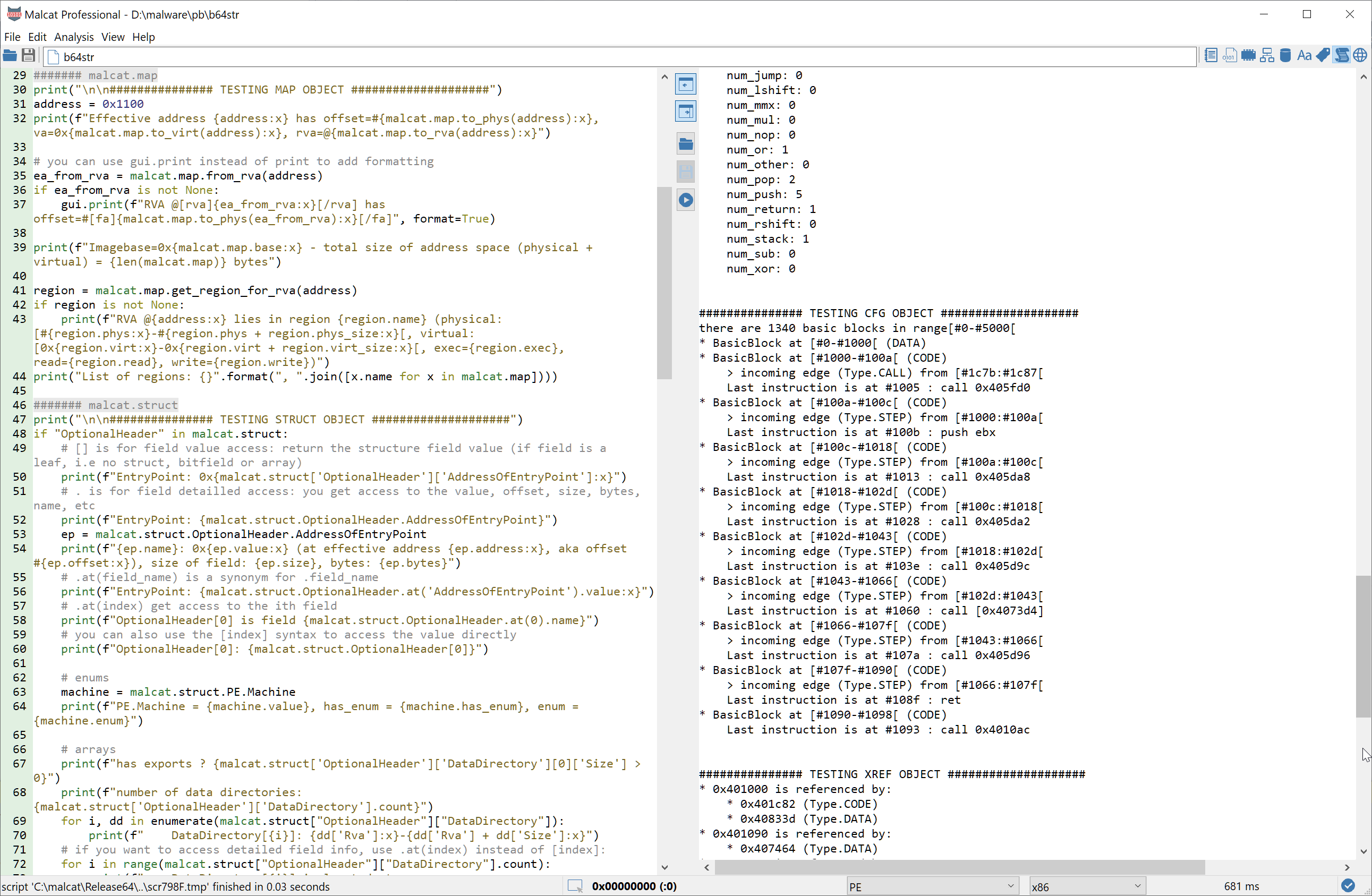
The complete result of the analysis is available via the scripting interface in a somewhat pythonic way. You have also the possibility to patch the file, or open arbitrary data as a sub-file directly inside Malcat. This should ease the development of quick-and-dirty unpackers, or just help malware analysts to statically deobfuscate a sample.
Joe sandbox lookup
Paid versions of malcat have access to the threat intelligence view (F9). It allows you to search the currently selected pattern against a corpus of local files, and to check the file's hash against a database of online threat intelligence service. We have now added Joe Sandbox to the list of online threat intelligence services. Make sure to enter your API key (public keys are ok) into Malcat's Options dialog, and run the online threat intelligence lookup (Ctrl+I).
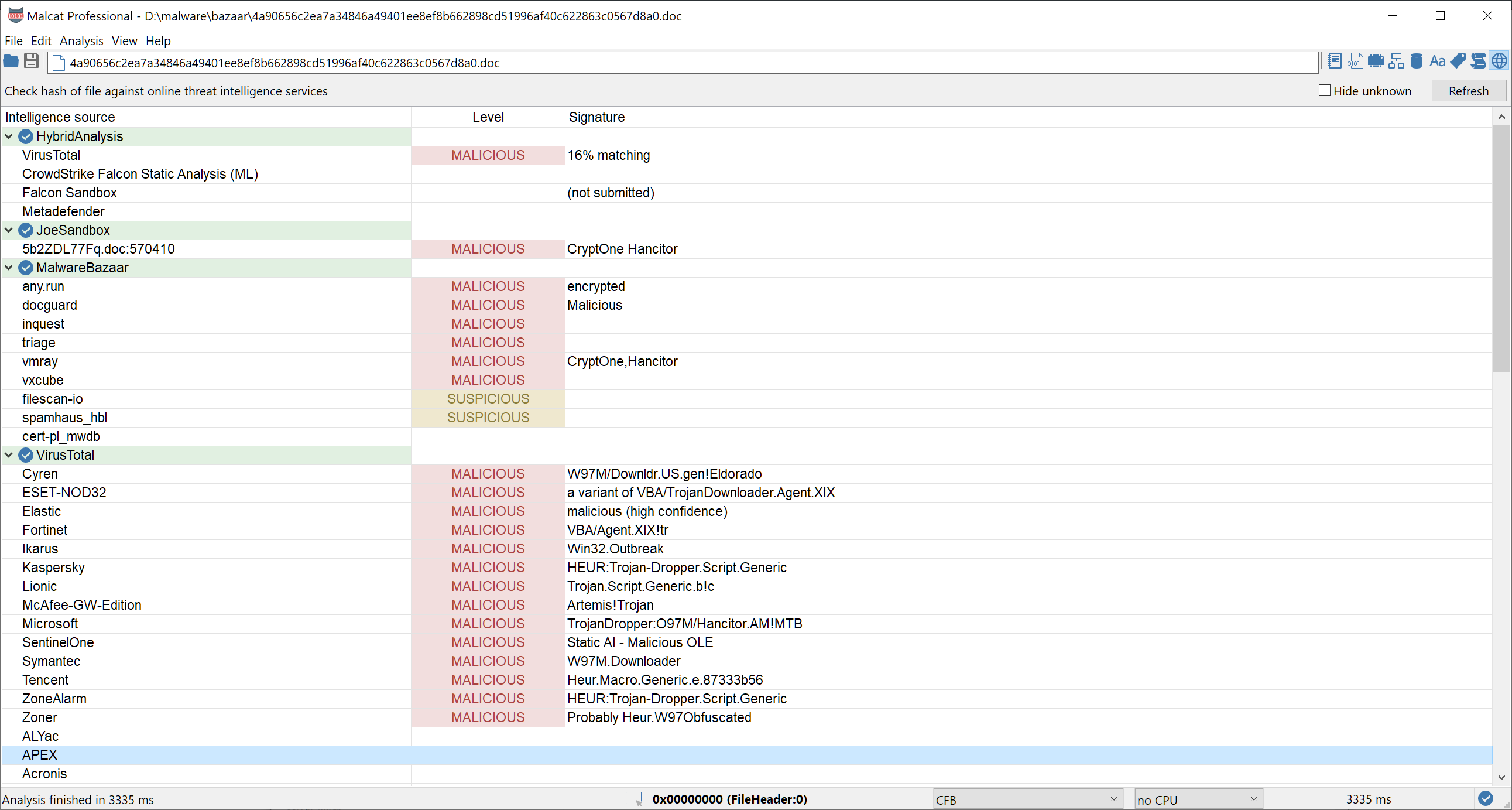
Full changelog
Here is the complete changelog of this release:
● Scripting:
- Cleaned up scripting interface a bit
- Finished scripting documentation
- Updated start script
- Script editor and Yara editor now use mono font
● MSI installers:
- Proper decoding of MSI stream names
- Can now decompile MSI tables (hit F4)
- Added msi.dll ordinal names (most MSI dll plugins use import by ordinals)
● Misc:
- Added JoeSandbox web API to online intelligence lookups
- Linux: Copying data now puts content in both PRIMARY and SELECTION clipboards
- Updated Yara rules
● Bug fixing:
- Fixed bug in PE+ import by ordinal handling
- Fixed HexView background not beeing redrawn properly on hover in some edge cases
- Fixed file path label in signature editor not respecting visual theme